Serial Fraud Monitor
Identity intelligence one step ahead of emerging threats
Protect your business from sophisticated, undetectable fraud.




Home » Serial Fraud Monitor

Powered by advanced neural networks, AU10TIX’s award-winning Serial Fraud Monitor has identity intelligence designed to combat coordinated traffic-level attacks, helping you to stay ahead of the game and ensure the safety of your business.
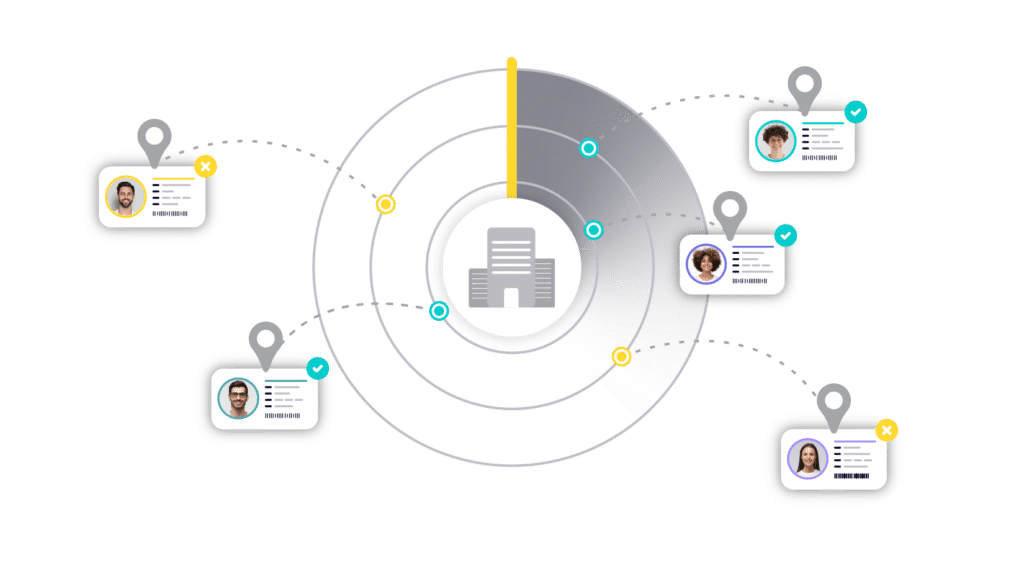
Identity intelligent systems save money by automating verification, reducing fraud, and cutting operational costs. Faster, more accurate detection prevents costly breaches, ensures compliance, and streamlines onboarding for efficient scaling.
Highly accurate fraud detection, leveraging machine learning and AI mechanisms to recognize even the most sophisticated synthetic fraud.
Detect deepfakes by analyzing behavioral patterns, anomalies, repetitions and conflicts.
Real-time fast reaction and insights that detect fraudulent activity based on incoming and historical traffic patterns.
Reputation scoring and data cross-checking in a consortium, utilizing millions of data points.
Tracks over 20 visual, data, and non-data vectors, such as background and geolocation, providing robust validation.
Check existing data blocks to identify fraudulent accounts and prevent existing threats.
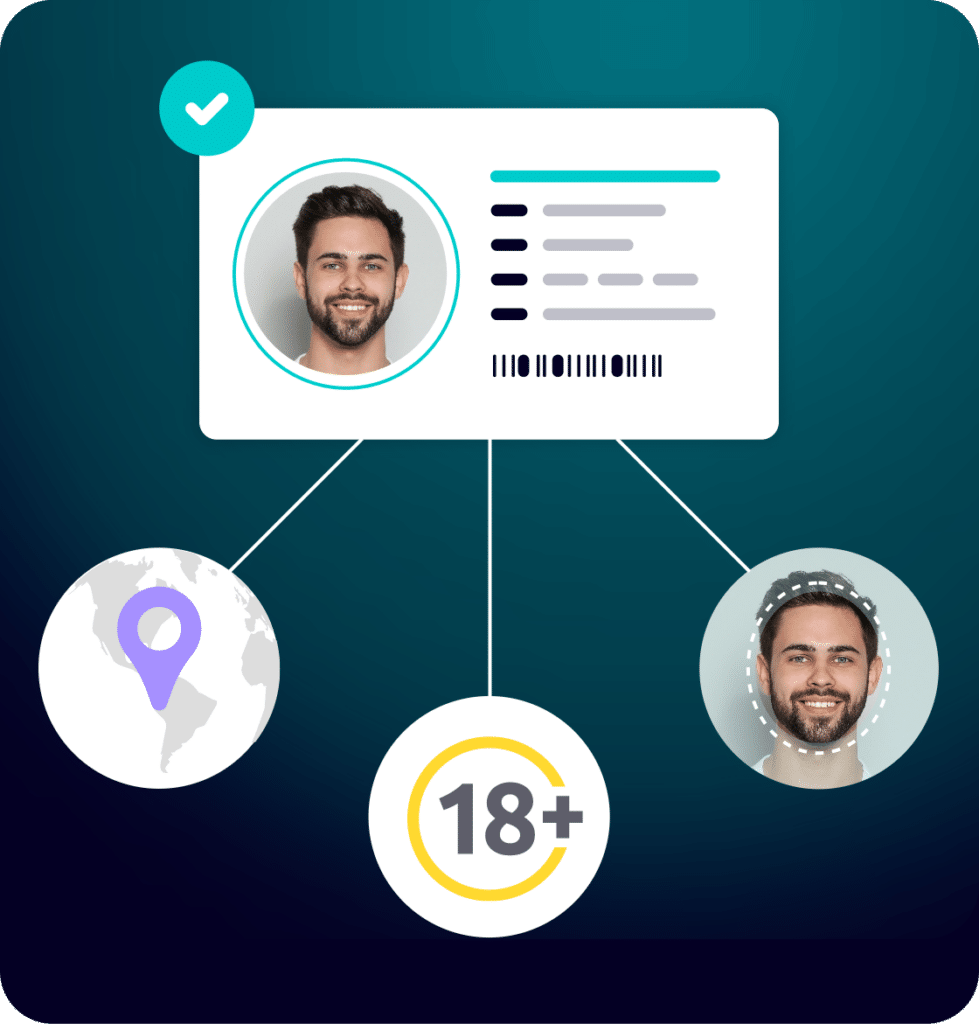
Detection using
advanced neural
network technology
Based on pattern
recognition and
repetition analysis
Continuous
monitoring with a
feedback loop
Reputation scoring
and data crosschecking

Fiverr found AU10TIX’s support impeccable. Their regular communication about technical changes, deployments, and any potential downtime ensured a seamless partnership. Working closely with the Customer Success Managers and their proactive availability, even in the same country, made the experience smoother.

We are excited for AU10TIX to take our company’s technology vision to the next level, enabling business growth for merchants and a secure shopping experience for millions of ShopBack Pay and PayLater users, whether it be in-store or online.

AU10TIX was the obvious choice for us to partner with thanks to their demonstration of unmatched speed and fully automated ability to detect complex fraud attempts that were unexpected by other verification providers. We are excited for them to take our verification capabilities to the next level.

Microsoft plans to include the Reusable ID technology in its third-party onboarding flow to streamline repeated validation of user identity verification at critical steps while preventing fraudulent activity and ensuring regulatory compliance.

Aspire Global has enjoyed strong collaboration with AU10TIX for years, so we felt the logical next step was to expand the service to our full portfolio of companies.
AU10TIX is the go-to identity verification solution for the hospitality industry, with a client base that includes the biggest names in the sector.

AU10TIX’s strategic collaboration with Microsoft in the decentralized identity space and their impressive track record of client satisfaction underscores their ability to deliver impactful solutions.
Collaborating with AU10TIX empowers businesses to verify information at scale while ensuring users have greater control over their personal information.

Last year, we partnered with identity verification company AU10TIX, to integrate its facial recognition technology to verify the identities of customers and new merchants. Deploying such technology has enabled us to counter the growing threat of fake identification documents that criminals are using to scam merchants and payment platforms.

Quickly integrate AU10TIX solutions with your existing systems using our flexible, low-code tools. From API and SDKs to WebApp integration, we offer multiple options to suit any business need and use case.

Reduce integration time to from days to hours

Ready-to-use web and mobile interfaces for enhanced UX

Easy-to-read JSON with data grouping for clearer representation

24/7 assistance to ensure smooth implementation